Don’t Take the Bait.

Amber Mason Originally published August 4, 2022. Updated on October 10, 2023.
What is a Phishing Attack?
A phishing attack is a type of social engineering attack, or an attack used to steal user data when a hacker masquerades as a trusted entity and tricks the victim into opening a text, email, link, or instant message that contains malware or can lead to a ransomware attack. Attacks like these can have devastating effects, as hackers gain access to lots of personal information such as credit card information, log-in credentials, addresses, and much more, leaving victims open to issues such as the stealing of funds or identity theft.
Phishing doesn’t just affect individuals, many attackers use phishing on employees to gain leverage in corporate or government networks as part of a larger attack, with most attacks aimed at gaining privileged access to secured data or bypass security perimeters.
How Does Phishing Work?
Phishing starts with a fraudulent email, text, or other communication designed to lure in the victim. The message sent is designed to look like it comes from a trusted sender such as a well-known company. If the victim is fooled, then she/he is coaxed into providing confidential information most often on a scam website. Malware may also be downloaded onto the victim’s computer through the victim interacting with the fraudulent message in some way. This is why phishing is one of the most dangerous cybersecurity risks your business faces.
Cybercriminals begin their attacks by first identifying what individual or group they want to target, then use emotions like fear, curiosity, urgency, or greed to compel the victim into opening attachments or malicious links by also posing as a legitimate company or person.
Email Phishing
Email phishing is the most well-known and common form of phishing attacks seen today. Hackers send emails to their targets impersonating a known brand/company, and create a heightened sense of urgency that leads people to click on a link or download an attachment that contains malicious content. Most often, links will lead to malicious websites that steal credentials or install malware onto the victim’s computer; attachments and even images can also contain malicious content that installs malware when opened.
Examples of Email Phishing:

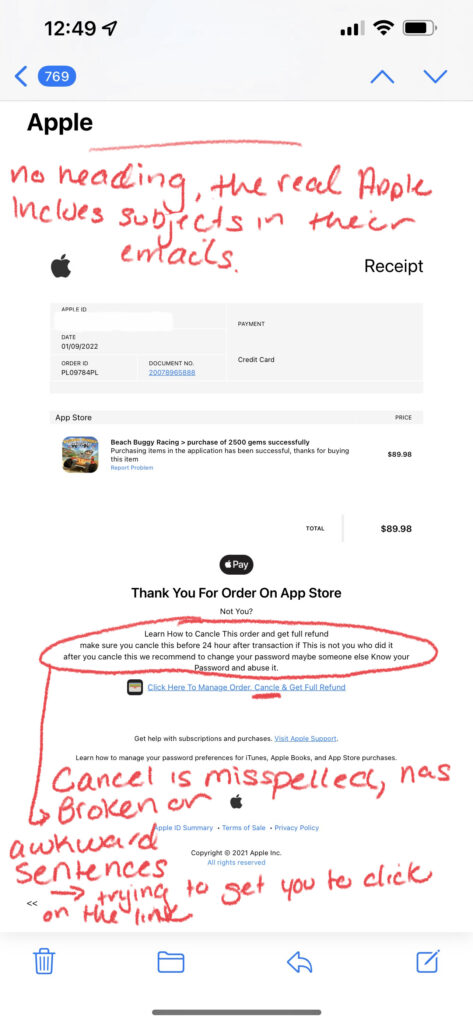
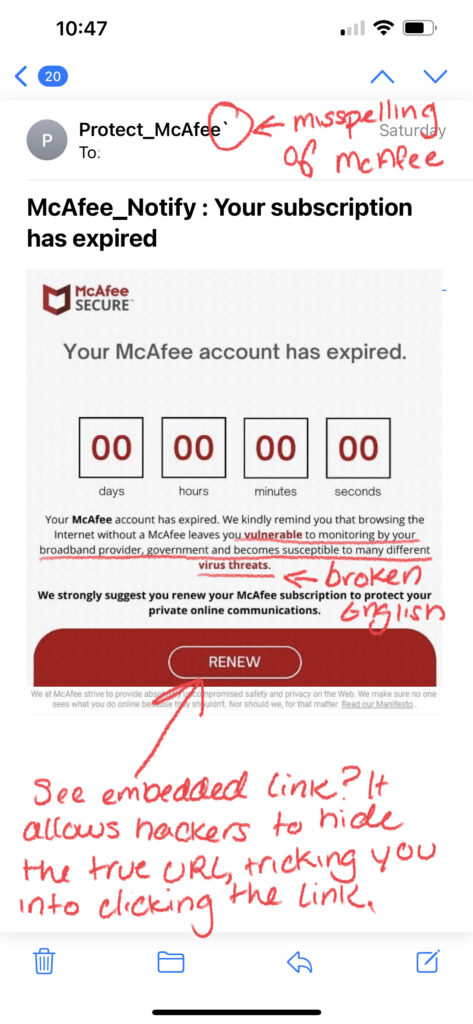
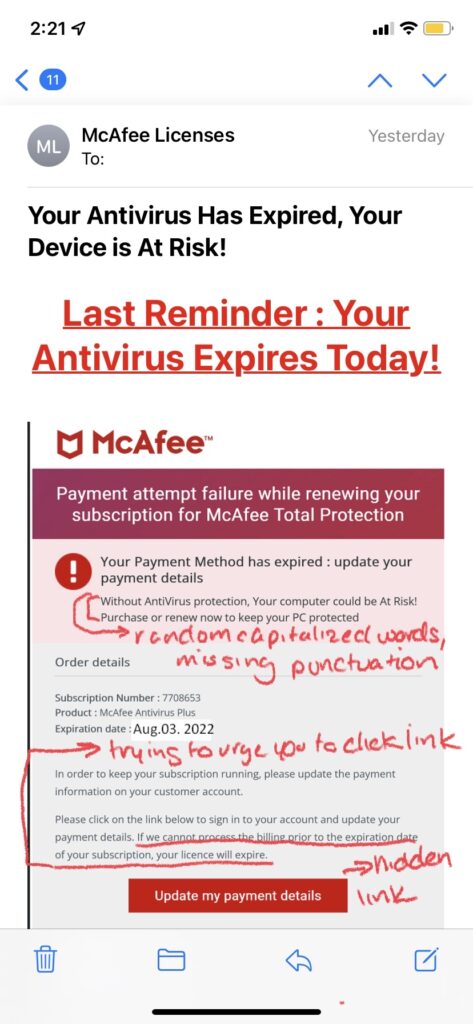
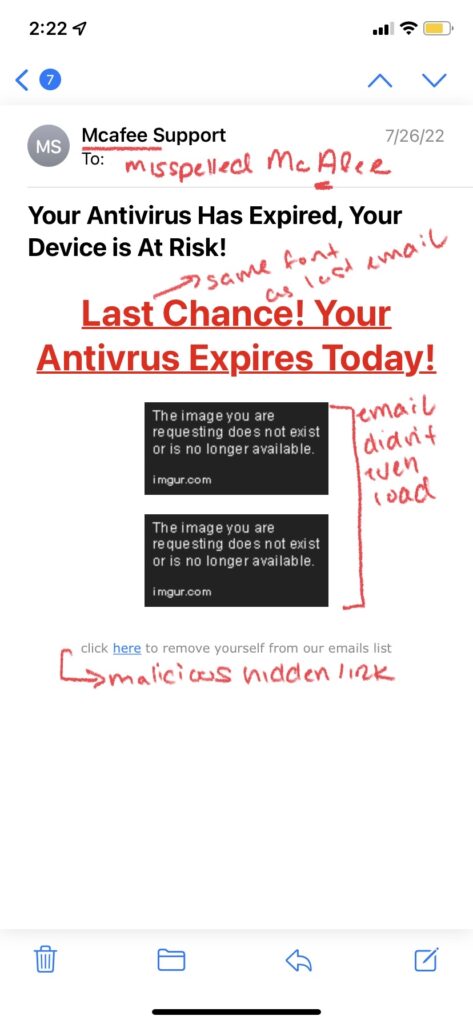
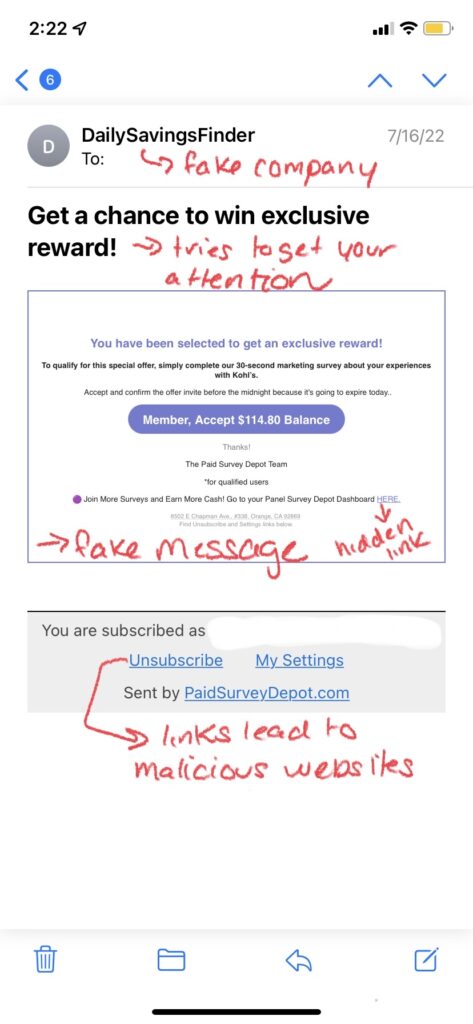
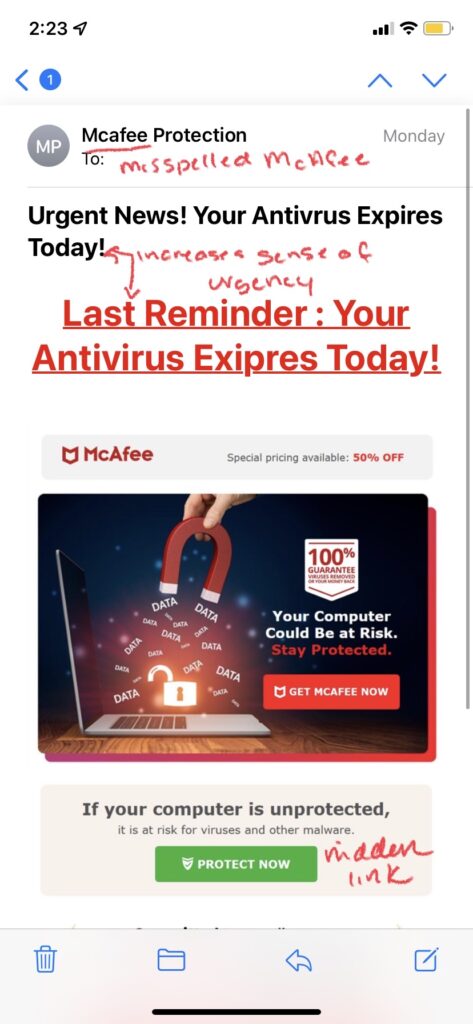
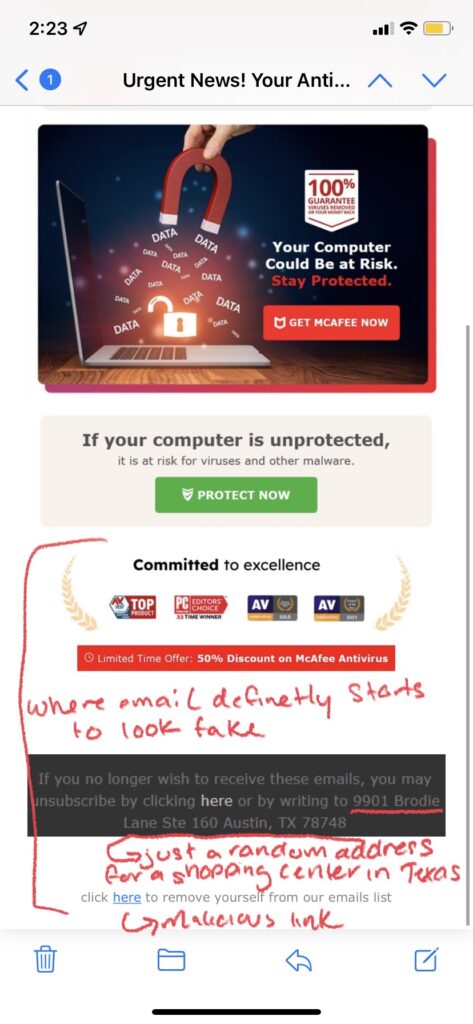
How to Spot a Phishing Email:
- Grammar/Spelling Mistakes: Many scammers are working from countries where English isn’t a dominant language, meaning spelling mistakes or grammar errors that are typically made by people who have learned English as a secondary language are more likely to occur. Awkward wording or sentences that don’t quite make sense are common signs of a scam email. However, you cannot rely on just grammar or spelling mistakes alone to single out a phishing email. Recently, a newer form of email phishing called clone phishing has surfaced, which is where a hacker copies an email actually sent by a real company, replaces links in the email with their own malicious ones, and then resend the email pretending to be the legitimate company. In this instance, grammar and spelling mistakes are nonexistent as the email was a legit one, so it is important to look for other tell-tale signs of an attack such as:
- Illegitimate Information: Hackers send these phishing emails from domains that have similar names than those of the company or brand they are trying to impersonate. For example, a hacker pretending to be Microsoft Support might send an email from the address domain @micrusoft.support. See how Microsoft is slightly misspelled with a “u” instead of an “o”? Anyone glancing at an email might not notice this slight difference, leaving them unaware that the email is fake. You should also review the email for any inconsistencies in branding throughout the email, such as a misspelling of the company name, an edited logo, or a layout/theme not typically seen from that brand or company.
- Shortened or Embedded Links: Another tell-tale sign of a phishing email is shortened or embedded links within the content. Many hackers stress the urgency of the email, prompting their victims to click on links without a second thought. Shortened links can bypass Secure Email Gateways, delivering malware right to your inbox. Embedded links are also something to be cautious of, as you cannot see where the link leads. Of course these links should be taken into consideration if you are already wary of the email, as legitimate companies still send links through email as well. In order to see where a link is leading, hover your mouse on it without clicking; this will display the full URL of where the link leads. However, it is also important to note that some cybercriminals create fake websites as well, so even if the link appears legitimate, you should proceed with caution.
Spear Phishing
Even though spear phishing utilizes emailing, it is a more targeted approach, focusing on businesses or companies. Cybercriminals start by using open source intelligence to gather information about employees from public websites and social media. They then use this information to target specific individuals within the organization/business by sending them emails using the real names, job titles, or phone numbers of people who work within that company to trick the recipient into thinking the email was from someone else within the organization. Because the recipient is tricked into thinking the email was an internal request, they are more likely to take the action mentioned in the email.
Examples of Spear Phishing:

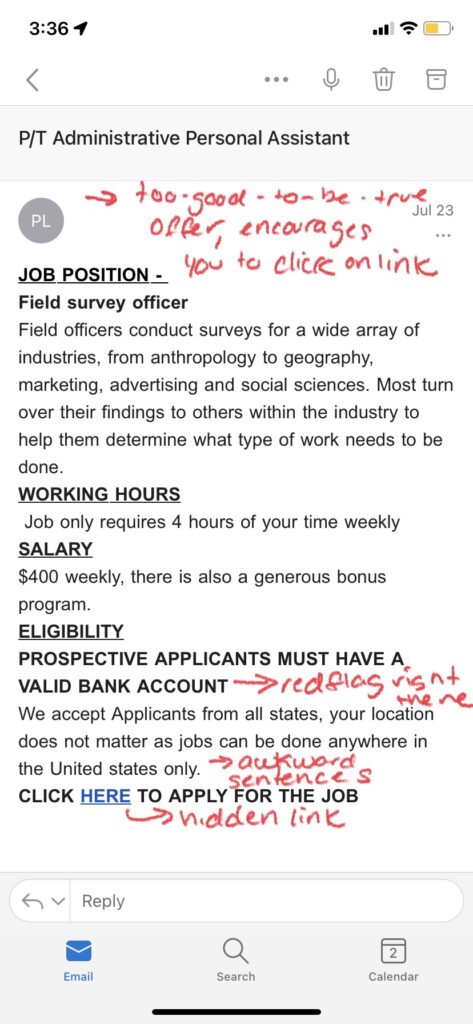
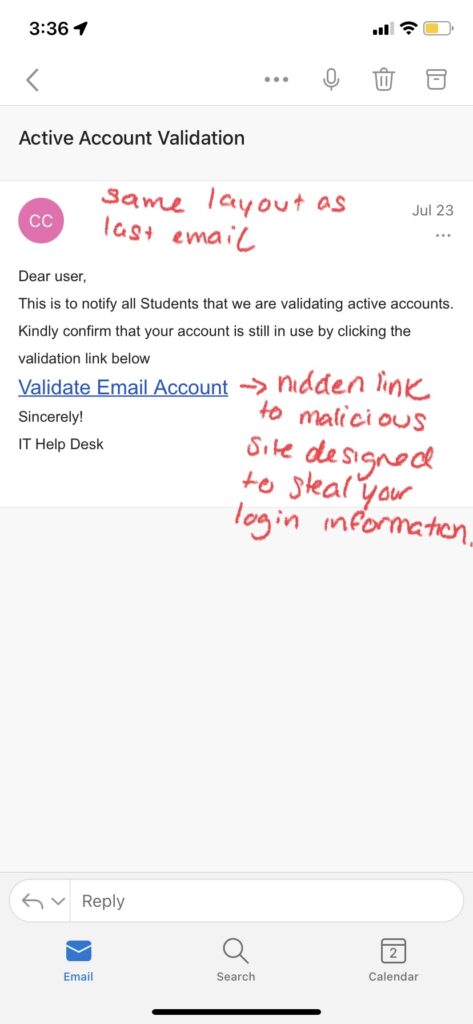
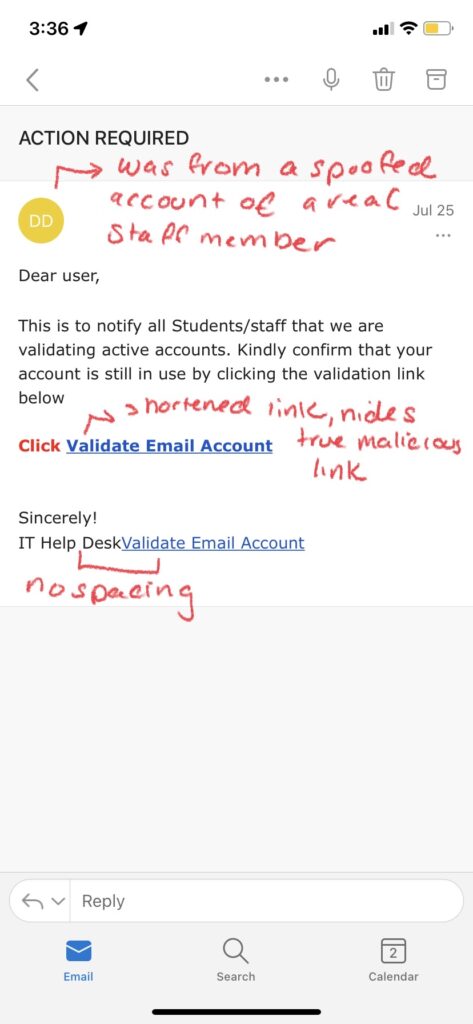
How to Spot Spear Phishing:
- Abnormal Requests: Look out for requests from people in your company that may seem out of the ordinary considering the person’s job function, or that ask for login credentials or personal information.
- Shared Links: Along with abnormal requests, you should also be wary of links to documents or attachments that are stored on shared drives such as Google Suite or Dropbox, as they often redirect to a malicious website or can install malware.
- Password-Protected Documents: Any documents that require a user login ID and password to view may be an attempt to steal your login information.
Whaling/CEO Fraud
Whaling is the same concept as spear phishing, but instead focuses on the higher-ups, like company CEO’s instead of any lower-status employee. The end process however is a bit different. To start, the hacker uses public web sources to find the CEO or other figure in a leadership position for the organization they are targeting, and then use that information to impersonate that CEO using a similar-looking email address. These types of emails typically ask for a money transfer or the request for the recipient to open an attached document (containing malicious content).
Examples of Whaling/CEO Fraud:
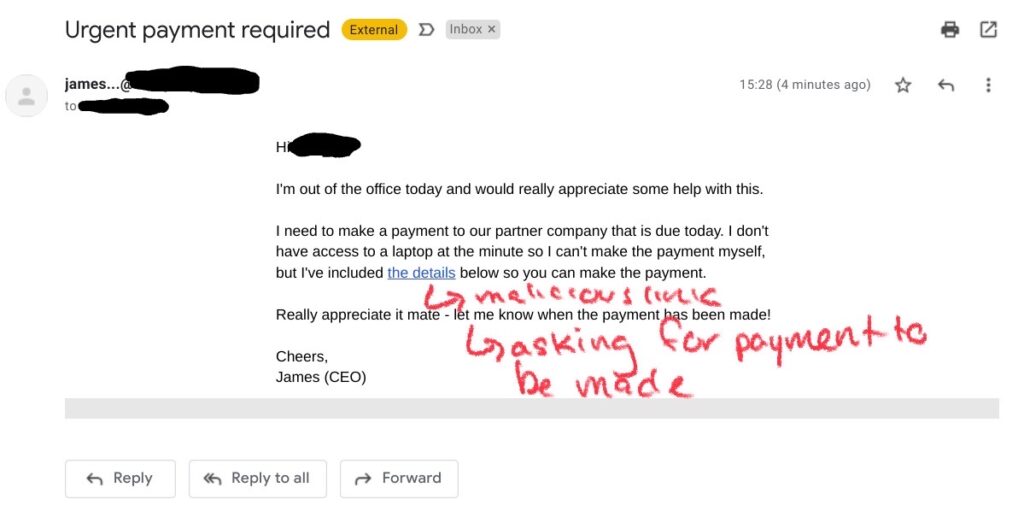
How to Spot Whaling/CEO Fraud:
- Abnormal Requests: If your company’s CEO/senior leadership member has never contacted you before, or is making an alarming request (such as the transfer of money or asking you to provide personal information like login credentials or a personal phone number), you should be wary. If you are unsure of an email or other form of contact from a person of leadership at your company (or even any employee), and you have another way of contacting that person, such as a direct phone number, confirming if they actually sent you an email or requested you to do something would be advised. Even if you are worried about not getting the task or requested information done, your boss/CEO will likely be much more grateful that you confirmed the legitimacy of “their” request, instead of blindly taking action.
- Suspicious Email Address: If your company has a regulated email address provider such as [email protected], and you notice the misspelling of the CEO’s name in the sender address or misspelling of the company name, it may be a sign of CEO fraud. Also, unless you have established communication with your leadership member through a personal email address before, any emails from your CEO with abnormal requests sent to your personal email address should be a cause for concern as well. Remember, it’s better to double check with the person that appears to be sending you emails to make sure it was actually them, rather than just immediately taking action. These hackers WANT you to blindly take action, and are counting on people within the organization to do so in order for the hacker to get what they want. By simply reaching out to the supposed sender to verify they are requesting you to take action or submit personal information (make sure you connect with them through another form of contact such as a direct extension within your company or a personal phone number provided by that person directly, NOT through the email they just supposedly sent you), you can save your company from the devastating effects of a successful phishing attack.
Vishing
Vishing, or more commonly called a “spam call”, is when a cybercriminal calls a phone number and creates a sense of urgency that makes the victim take action against their best interests. These calls can happen at any time, but are more commonly seen around stressful times, such as tax season. For example, many people receive spam calls from hackers pretending to be the IRS, stating that they need to do an audit and request your social security number. Because this creates a heightened sense of urgency, the victim is often tricked into providing the requested personal information. The important thing to remember is a trusted company will never request any sort of personal data such as a social security number or bank account information over the phone.
Examples of Vishing:
How to Spot Vishing:
- Caller ID: Fraudulent phone calls typically show up as an unknown number, or a number from an unusual location; if you live in the U.S., a random phone call from a number outside your state or the country is most likely fake. A good rule of thumb is unless you were expecting a phone call from a new phone number, any calls from unknown numbers even within your state are most likely fraudulent, and should be sent to voicemail.
- Requested Action: If the caller is requesting personal information such as your SSN, bank login credentials or routing/account number, or credit card details, it is not a legitimate phone call. As stated before, a reputable company or brand will never request your personal information over the phone, especially that which has to do with banking.
- Timing: These types of scams are more numerous in times of stress, so if you receive an abnormal call during times such as tax season or the holiday season, it is most likely fake. These hackers are preying on these stressful times, and use that stress to further push you to blindly take action in order to give the cybercriminal what they want.
- Tech Tip: If you’re unsure of an incoming phone call, let it go to voicemail! If the caller was a trusted contact, such as a doctor’s office or a new friend calling, they will most likely leave a voicemail. If the caller does not leave a voicemail, or leaves a voicemail with no one speaking, it is most likely a scam and does not warrant a call back or any further communication.
Smishing (SMS/Text Scam)
Smishing is just like email phishing, but through SMS messaging or text. The hacker pretends to be a reputable company, and will often request personal data or ask you to click on an attached link, which can install malware on your device.
Examples of Smishing:
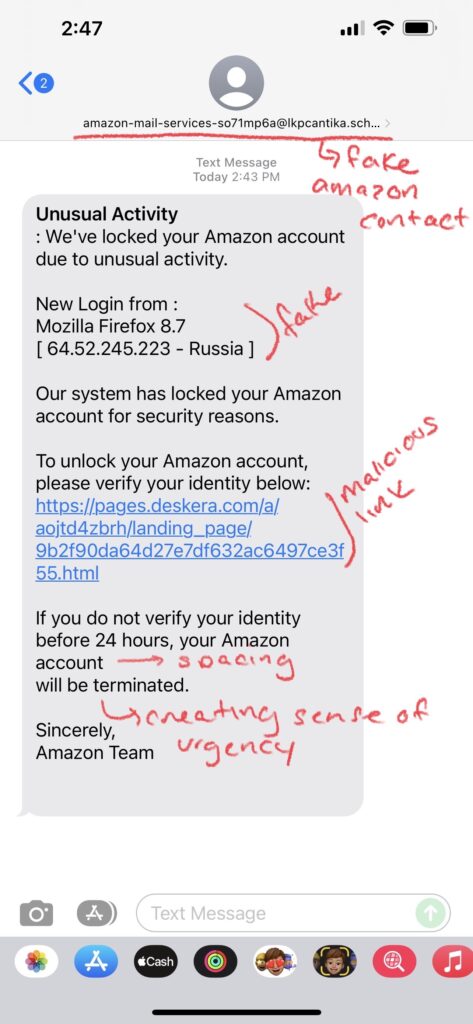
How to Spot Smishing:
- Delivery Status Change: The most common form of fraud texts are ones telling you to change a delivery or ask you to provide more information on your address (usually from Amazon). If you are unsure of a text regarding a package you ordered, you should always check the actual website you ordered from to check the real status of your package. You should never click on any link or document attached in a suspicious-looking text.
- Abnormal Requests: As with any phishing attack, any sender asking you to provide any personal information should be considered with caution. Typically, any text from a number requesting action from you and is not already in your contacts should just be ignored.
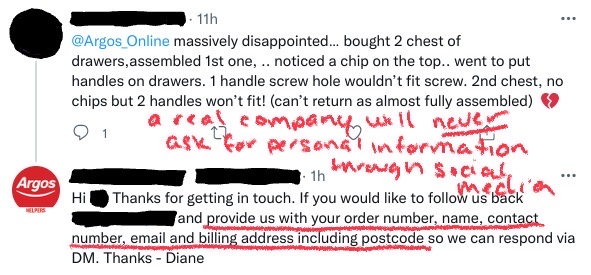
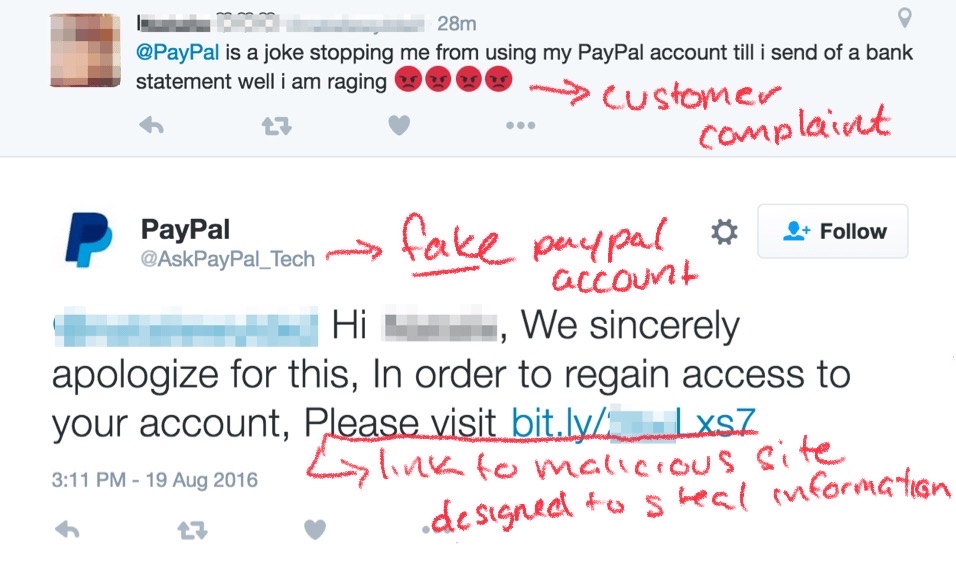
Angler Phishing
Angler phishing occurs on social media, when a hacker uses direct messaging through apps like Instagram to trick the victim into taking action. These hackers will create fake accounts pretending to be a customer service representative, and then try to lure their victims into handing over access to personal data or account details. Angler phishing typically starts with a commented complaint from a real customer on the company’s actual page. The hacker will then reply to that comment pretending to be a customer service representative from that company, typically a financial institution like a bank. The hacker will reach out to the complaining customer via the comments or DM, offering very faux friendly and understanding support, immediately providing a link to be taken directly to a representative who’s standing by and ready-to-help. Sounds too good to be true, right? Well, it is. When you click the provided link, instead of taking you to a representative, it can install malware on your device, take you to a video streaming site (often with some not-so-suitable-for-work content), or to some other site that aims to get money and information from you.
Examples of Angler Phishing:
How to Spot Angler Phishing:
- Comments/Direct Messages: If you’ve left a complaint comment on an official business’s social media page, be wary of any replies you receive on that comment, or any DMs you receive related to that comment, especially if it’s from a “customer service representative”. Never open links or DMs from an account you do not know or recognize, and if you are unsure, make sure to check the verification of that account. However, it is just a better idea altogether to take any issues you have right to the company’s customer service department, which avoids the angler phishing scam altogether. Help can most commonly be found on the company’s website, where you can communicate with a real agent about any concerns you may have.
How to Prevent Phishing
Cybercrime continues to rise, and phishing scams can do a lot of damage to your or your company. Knowing how to keep yourself and/or your employees safe from attacks is a very important task. Having support from an IT company with offered managed services is highly recommended. Let’s take a look at why:
- Educate Yourself and Your Employees: The first line of defense against any cybercrime is to be aware and actively paying attention for any suspicious activity. Cybercriminals are advancing their methods everyday, so it is very important to keep yourself and your company up-to-date and aware of new and old attacks. An IT support team such as Monmouth Cyber can offer regular training and tutorials on cybersecurity procedures and any other new or upcoming attacks to be aware of. Cybercriminals are always developing new ways of stealing information or money, so keeping up-to-date helps ensure that you and/or your company will be protected before an attack happens.
- Update Your Devices: Keeping your devices updated to the latest software ensures that you will be less susceptible to attacks; as computers or other devices go out-of-date, it becomes easier for hackers to access your device and data. An IT company should be offering regular maintenance visits as part of their offered services; at Monmouth Cyber, we regularly perform maintenance (every 3 months for businesses) on all your computers to ensure that they are up-to-date, secured, and virus-free. Regularly maintaining your computers is highly recommended as machines in general need consistent care and service – much like your car – and can help stop a problem before it starts.
- Install Antivirus Protection: Having antivirus and security protection on your computers is a must-do. Along with ensuring that your data is protected, antivirus protection also protects your private personal information (like bank details) from peering eyes. An IT company can help install virus protection, and even set up remote monitoring, meaning that they actively monitor your network’s security to catch an attack before it happens.
- Have A Back-Up Plan: Having an IT company on call is a big factor in whether you are affected by a cyberattack. However, some attacks are inevitable, so what should you do when this happens? Having a disaster recovery plan in place ensures that in the event of an emergency, you will not be left in the dark. This may entail a backup of important data, or even a step-by-step plan of how to proceed next. A disaster recovery plan should be discussed and made with your IT support company, where they can offer suggestions or steps to follow in the case of an emergency.



