Amber Mason Published September 5, 2022. Updated October 13, 2023.
Beware of Malware! Malware is used to describe any applications or code that can damage or disrupt your device and its functionality. When a device becomes infected with malware, you may encounter compromised data, unauthorized access, or being locked out of your device until you pay a ransom. Cybercriminals, or the people who distribute malware, are motivated by money and will use malware-infected devices to launch attacks to obtain data like banking credentials and personal information that can be sold (such as your SSN), as well as to sell access to computing resources or to coerce payment information from victims.
How Does It Work?
Malware works by using trickery to disable or impede the normal use of a device. Once a cybercriminal has gained access to your device through either one or a few methods such as sending you phishing content (Check out our blog on that here), visiting a malicious website, downloading an infected file, and more, they will take advantage of that situation by launching additional attacks aimed at obtaining data such as account credentials, personal information, payment information, and more. These attackers can also use malware to take control of or lock you out of your device.
Anyone can become a victim of a malware attack. Although some people may know how to spot certain ways hackers try to deliver malware such as through phishing emails, cybercriminals are constantly evolving and improving their methods, so even the most up-to-date person might miss an attack. Malware attacks also differ greatly, so one type of malware might look and behave completely contrary to what another form of malware might be doing; you might not even know it’s there!
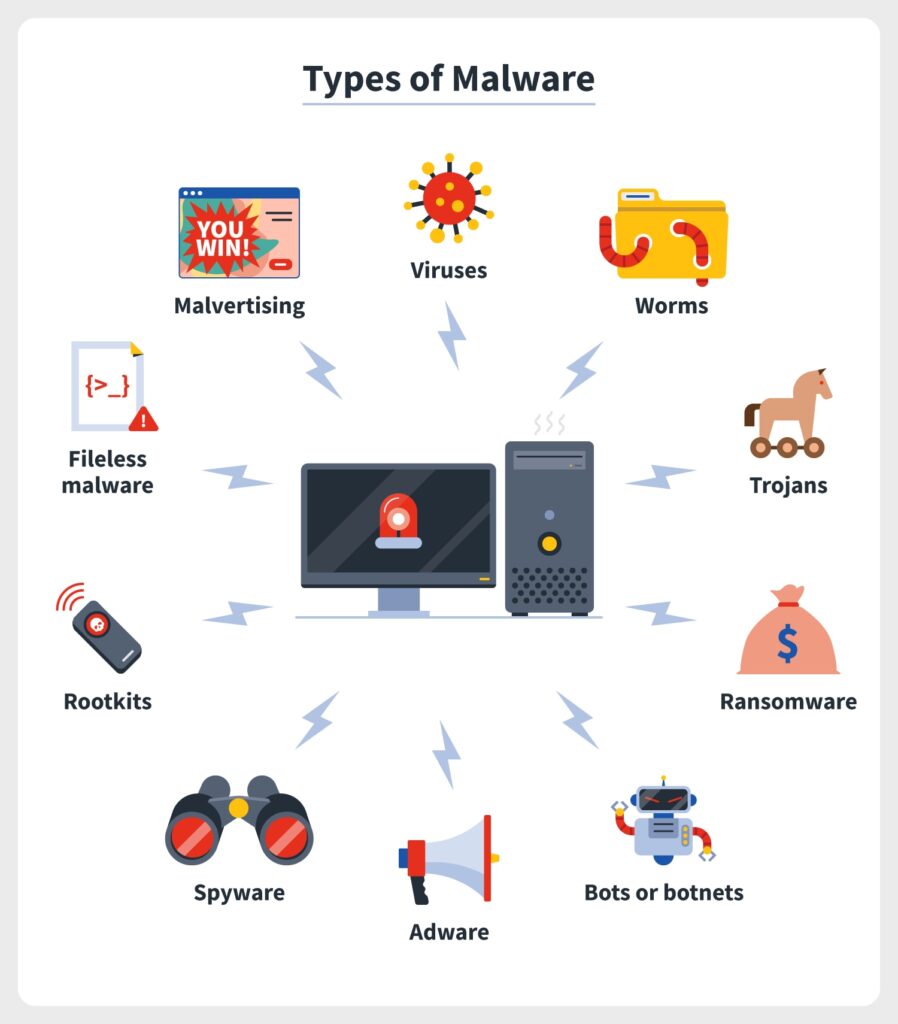
Types of Malware
Malware is constantly changing and evolving, making it difficult to narrow down the different forms of attacks; over time, some malware types have become hybrids of one another, making them even more difficult to identify. However, there are some commonly spotted forms of malware that may help you identify other, more complicated malware types.
Malware Viruses
Viruses are a type of malware that delivers a piece of malicious code that has been inserted into an application, program, or system and has the ability to self replicate and spread to other devices. Malware viruses are activated by the victims themselves, meaning that the user must click on, visit, or interact with a piece of content containing malware for it to start working. Viruses can be spread through malicious links sent in phishing attacks, embedded in legitimate software or file downloads, hidden in online popups, spread through outdated software, and more. These viruses are much like the bodily viruses that humans experience because they require a host (aka, a device) to live and can spread from device to device. Malware viruses lie dormant until triggered to attack, perhaps from users downloading an email attachment with the virus attached, or clicking on an image on a malicious site. Once triggered, the virus replicates and spreads copies of itself from computer to computer, infecting a whole network.
Overall, malware viruses can:
- Seize or disrupt applications
- Steal or even completely delete your data
- Send infected files to contact lists
- Send emails from your inbox without your consent, often embedded with the virus
- Launch ransomware attacks
- Launch DDoS (distributed denial-of-service) attacks
- Corrupt files and software programs
- Overall effect the speed and performance of your device
Worm Malware
Similar to malware viruses, worm malware can self-replicate, but unlike a virus, it requires no human interaction to do so once it has breached a system and does not require a host device or program attach to to cause damage and replicate. Malware worms can be spread through software vulnerabilities (hackers will inspect the codes of programs and softwares to see if there are any weak points where they can inject the worm, typically is found in outdated softwares – this is why you should always make sure your devices and programs are up to date), installed by removable media such as an external USB drive, spread through internet connections on shared networks (like the public WiFi at a Starbucks), or attached in malicious emails, texts, or direct messages. Once those attachments sent through email, text and more are opened, they could lead to a malicious website containing the worm or automatically download the worm malware. One the worm is installed, it silently infects your computer or even your entire network without you knowing.
Overall, malware worms can:
- Delete or modify files
- Steal data
- Infect many computers at once
- Launch DDoS attacks
- Launch ransomware attacks
- Create botnets
- Install backdoors for hackers to access your devices and data
- Install other forms of malware, such as adware or ransomware
Trojan Malware

Trojan malware is malware disguised as trustworthy and bon-a-fide software, applications, or files. This form of malware relies on using deception to trick the user into downloading what they perceive to be a real file, app, or program, but are really fronts used to disguise the real malware. Trojans are most commonly found attached in malicious emails, or hidden in popups or linked on websites and are installed when the user interacts with those links or opens attachments. Once installed, the trojan malware can perform the action it was designed for, whether it be to damage, disrupt, steal, or inflict some other harm on your computer or network. Like viruses, trojans require human interaction to be activated, but do not self replicate.
Overall, trojan malware can:
- Delete, modify, or steal data
- Spy on users
- Access networks
- Take remote control of devices
- Launch DD0S attacks
Ransomware

Ransomware is a type of malware that locks the user out of their device or files in exchange for payment to restore access to those files or device. Ransomware is most commonly downloaded through clicking on malicious email attachments and links or downloaded through malicious and/or pirated software (this is why you should never download software or content from untrustworthy sites, and if an offer seems too good to be true, such as a site offering a free download of Microsoft’s paid Office 360 software, then it is almost guarenteed to be a front for some type of malware, most commonly ransomware.). Once installed, the ransomware creates a backdoor for a hacker to enter your computer and begin encrypting data or locking you out of your device until you pay a ransom to regain access and/or ownership. Often, the ransom is demanded in bitcoin or another form of cryptocurrency. If the user fails or refuses to pay the ransom, then the hacker most commonly will delete your data so you can never access it again. However, you should NEVER pay the ransom, as there is no guarantee that the hacker will actually return your data after getting paid, and they commonly ask for a substantial amount of money/currency; instead you should contact a cybersecurity expert to remove the malware.
Overall, ransomware can:
- Hold devices hostage
- Encrypt data to make in inaccessible
- Result in financial loss
Malware Bots or Botnets
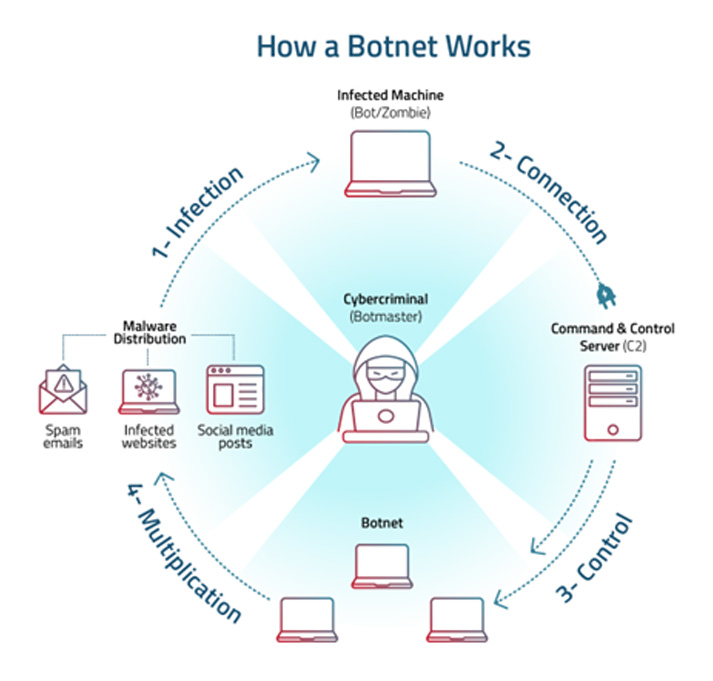
Bots are automated programs designed to carry out a specific task, they can be good (like chatbots or shop bots) or bad (like zombie bots – used to give hackers control of your device to create a network of infected devices, called a botnet, or scalper bots – ones criminals use to buy up the stock of an item, only to try and resell it for more than it’s worth). Malicious bots act as a sort of “spider”, meaning the bot program “crawls” through the internet looking for holes in security infrastructures to attack automatically. A malicious bot is designed to infect a host (device) and steal information. Some simpler malware bots include file-sharing and spam bots. A file-sharing bot takes a query term from a user such as a popular movie or album, responds to the query stating that they have the movie/album for download, but when the user clicks on the provided link, they are infected with a malicious bot instead. A spam bot will flood your inbox or DMs with unsolicited messages, most commonly from aggressive advertisers. Bots have the ability to create a botnet – A botnet is created by individual zombie bots, where the bots spread and infect thousands of computers, creating a network of infected computers/devices that different hackers can “rent out” to other malicious actors to carry out malicious attacks across thousands of computers at once.
Overall, malicious bots and botnets can:
- Record activity such as keystroke and webcam use, as well as taking screenshots of your device in use
- Send phishing emails from your device
- Give hackers remote control of your device(s)
- Launch DDoS attacks
Adware Malware
Adware is an advertising malware that spams and displays unwanted advertisements on your computer and more recently on your phone, most often as a pop-up that tracks your browsing activity to send you targeted ads. Some of these adware programs can be used for simple marketing purposes and aren’t necessarily malicious, but things go bad when cybercriminals use adware to collect your data to be sold to third parties online or to use against you to perform credit card fraud or identity theft. Adware is most commonly downloaded to your device when you install a program or software online, or click on a malicious popup.
Overall, malware adware can:
- Install spyware
- Share user data with third parties
- Attract users to malicious sites
- track your online activity
- Spam your desktop with unwanted ads, fake messages, and popups
How To Prevent and Detect Malware
Use Multi-factor Authentication
Multi-factor authentication (MFA) adds an additional layer of security to your accounts by introducing another step in the sign-in process. Most often, this extra step is a one-time code used to verify your identity that is sent to your mobile number that you are prompted to enter before the login process is complete. For more information on MFA and 2FA sign-in processes, check out our blog here.
Avoid Suspicious Emails, Links, and Websites
If you’re unsure of an email, advertisement, attachment, link or other form of media you see online, don’t click on it! It could be a phishing attack used to deliver malware.
Keep Software Up to Date
Keeping your software up to date is very important. Software updates repair security holes that cybercriminals can exploit. You should update your computer or device as soon as you can once a new update comes out, or you can turn on automatic updates to avoid the hassle of trying to remember.
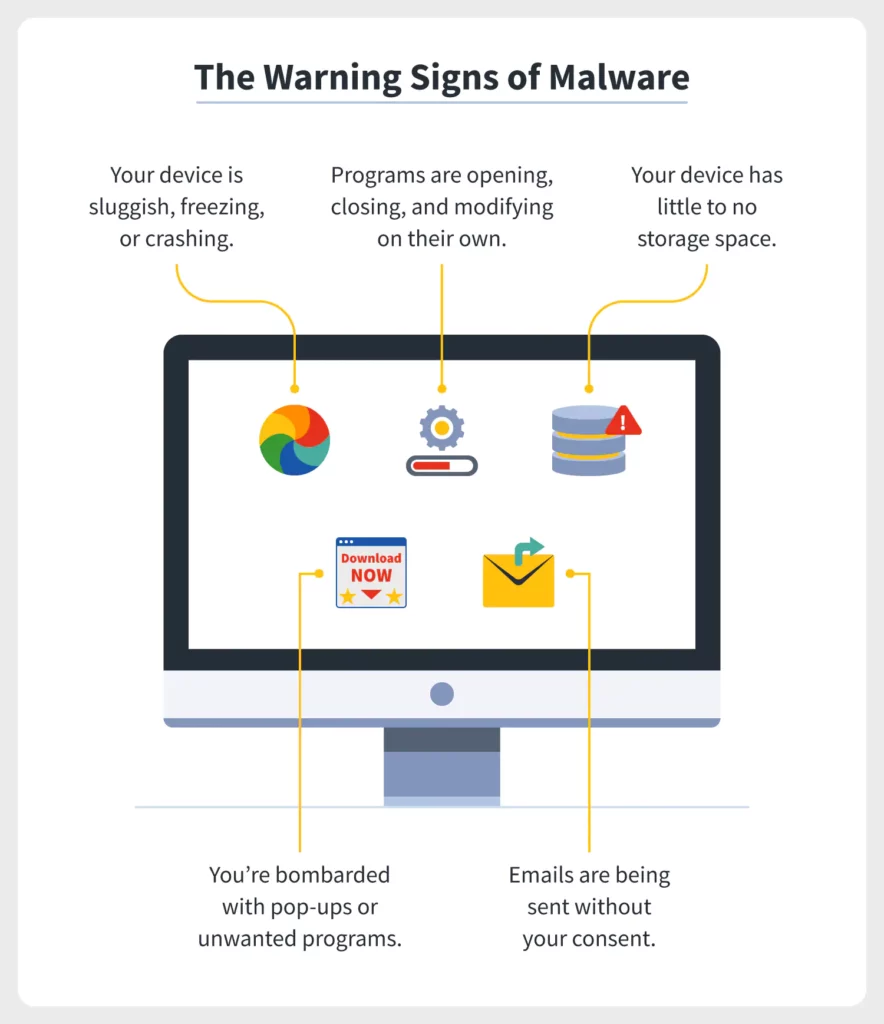
Know the Warning Signs
Being alert and aware of the warning signs of a malware attack can help protect your data and your device. Some warning signs to be aware of are:
- Your computer or device is freezing, sluggish, or crashing
- Emails are being sent without your consent
- Your device suddenly has little or no storage space
- Programs are opening, closing, and modifying themselves
- Your device is flooded with pop-ups or unwanted content
Install Antivirus Software
Antivirus software can help protect your device and data from malware attacks by monitoring and stopping cyber treats before they occur.
Regularly Back Up Files
Backing up your files and information can help prevent data loss in the event of a malware attack (such as a ransomware attack). Having a back up of your data also ensures that in the event of a power outage or computer issues, your information will be secure and saved.
Removing Malware
If you suspect that your device has been infected with malware, having a professional IT technician to help is definitely recommended. Malware can be tricky and almost virtually undetectable, so removing it is not an obvious task. Our technicians here at Monmouth Cyber are seasoned experts in removing malware and resetting your computer after an attack, and will ensure your device is protected against any further attacks. Give us a call to schedule malware removal, or to have one of our techs preform a maintenance visit (recommended for all computer users AT LEASt once a year to ensure your device is up to date and secure).
Additional Resources
To extend your learning beyond the basic information covered in this article, be sure to check out these additional resources.
- What is a computer worm? An in depth look from Malwarebytes.
- Trojan Horse software explained by Fortinet.
- Trojan horse – virus or malware? Defined by Malwarebytes.




